Welcome back Hackers!
In this post i will show you, how i found a vulnerable Russian Mission Control. We're going to work with shodan.io so make sure you create an account, its free. Lets get started!
Searching
I was searching for Russian Satellites but with one of the searches i used, i accidentally found a vulnerable Russian Mission Control. I don't know what kind of "Mission Control" it is yet, but i will analyse better and bring a part 2 of this post.
Syntax i used: "title:"Mission Control" country:"RU"
Results:
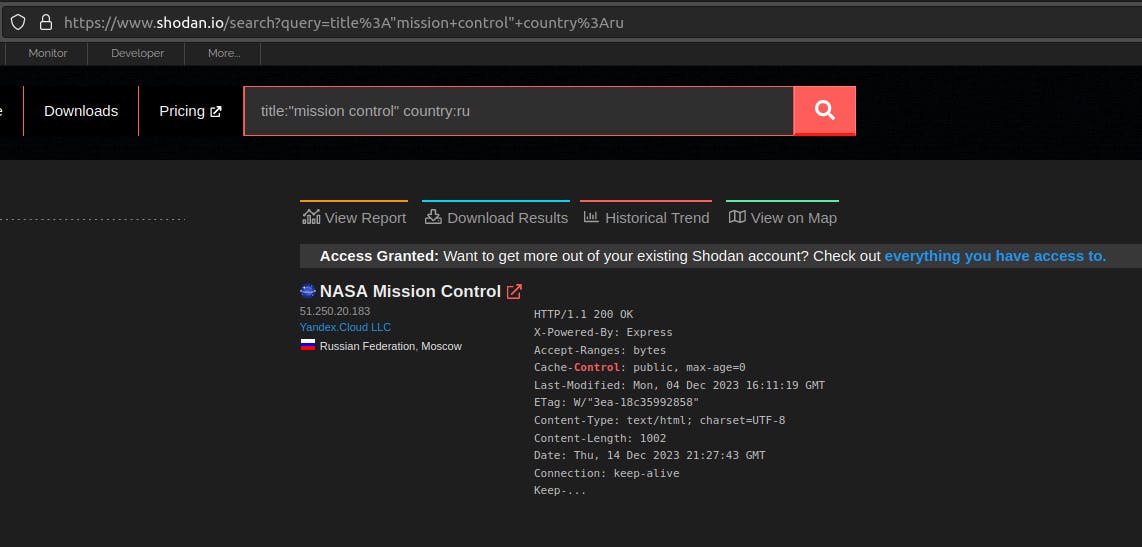
Ports open:
22
80
8000
8080
I analysed and found out that this system is an eol-product. An end-of-life product (EOL product) is a product at the end of the product lifecycle which prevents users from receiving updates, indicating that the product is at the end of its useful life (from the vendor's point of view). At this stage, a vendor stops the marketing, selling, or provisioning of parts, services, or software updates for the product. The vendor may simply intend to limit or end support for the product. In the specific case of product sales, a vendor may employ the more specific term "end-of-sale" ("EOS"). All users can continue to access discontinued products, but cannot receive security updates and technical support, and thats why it have so many vulns.
Locating
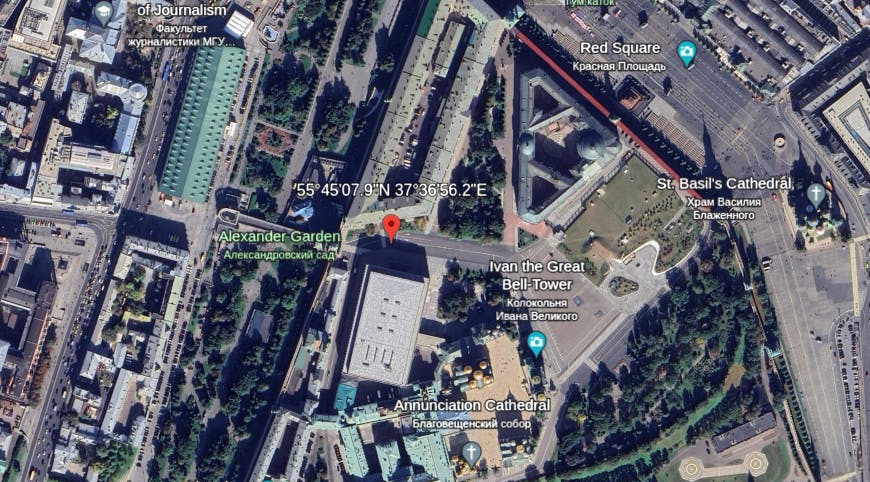
We know that this system is in Russian territory, but where exactly? lets find out.
We could use any website to locate the ip but i decided to create a basic python tool that locates it.
Thats what my tool shows me:
"ip": "51.250.20.183",
"city": "Moscow",
"region": "Moscow",
"country": "RU",
"loc": "55.7522,37.6156",
"org": "AS200350 Yandex.Cloud LLC",
"postal": "101000",
"timezone": "Europe/Moscow"
Scanning
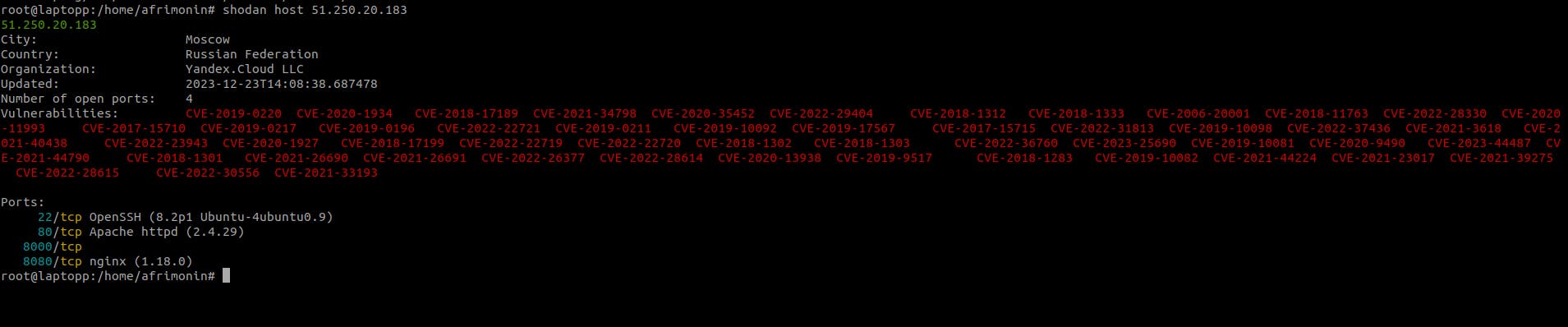
It's time to scan this system for vulns but i will not interact with the target, i will just use the shodan command line.
To do this we'll use the following syntax: shodan host 51.250.20.183
Results:
I will analyse everything better and bring a part 2 of this post, but now you have a basic understanding on how to search for vulnerable Russian systems.
Please leave a comment with a feedback and tell me what kind of tutorials you want me to bring.
Stay safe hacker!